FISMA follies
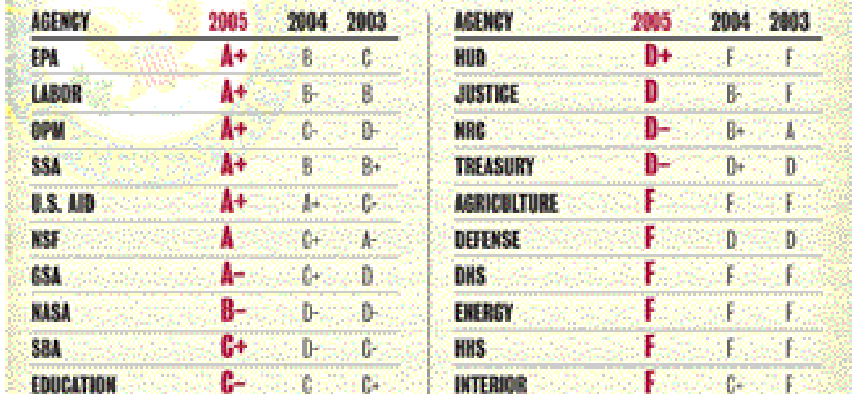
Bob Lentz wants to emphasize that FISMA is a good thing. The Federal Information Security Management Act requires federal agencies to report to the Office of Management and Budget and Congress on their progress in improving information security. But his department earned an F this year, and has never gotten higher than a D.
Bob Lentz wants to emphasize that FISMA is a good thing.The Federal Information Security Management Act is the law that requires federal agencies to report to the Office of Management and Budget and Congress on their progress in improving information security.Since 2001, agencies have been held up annually to public scrutiny, as Rep. Tom Davis (R-Va.), chairman of the Government Reform Committee, presents the grades the committee gave agencies based on their efforts to meet the act's requirements.Lentz, assistant secretary of defense for networks and information and integration, and director of information assurance for the Pentagon, sees the benefit of requiring agencies to report to Capitol Hill annually on their progress.But because his department earned an F this year, and has never gotten higher than a D, Lentz chooses his words carefully, because he knows first-hand the money and manpower the Defense Department is putting into improving cybersecurity."The Department of Defense uses FISMA as a critical management and assessment tool," Lentz told Davis at a hearing last month. "We continue to enhance our FISMA effort, consistent with guidelines from OMB."But after the hearing, Lentz said that while the FISMA grades raise the visibility, and thus the importance, of cybersecurity issues, they don't address whether an agency has improved cybersecurity."At times, we get a little too hung up on the score, and we make a lot of auditable, black-and-white decisions that end up not portraying" the true security picture, Lentz said.The grades "certainly are a factor in how you improve, but you have to step back" and ask yourself if the overall assessment you're making really is the whole picture, he said.Dennis Heretick, the Justice Department's chief information security officer, agreed on both counts: FISMA is important, but the grades may not reflect accurately an agency's cyber-readiness.Heretick is unhappy that his agency's grade fell from a B- last year to a D this year. He feels an A- would be far more reflective of the status of its systems."We improved sharply, in my opinion, in just about every one of the FISMA questions," Heretick said.For example, the Justice Department last year had a certification and accreditation rate of 91 percent; this year, it rose to 99 percent, he said.His agency's problems arose with its inspector general, who is responsible for assessing the condition of its systems, answering FISMA questions for OMB and preparing numerical scores for grading purposes, Heretick said."If you take the IG's view, if you have weaknesses, you deserve to be marked down," he said. "But if you want to fix things, you have to find the problems."This is part of a problem that Lentz, Heretick and others have observed: The scoring process is based on system-by-system assessments and doesn't include ways to get credit for enterprisewide infrastructure improvements.At the Defense Department, implementing the provisions of Homeland Security Presidential Directive 12, which requires all agencies to begin issuing interoperable smart identification cards by Oct. 27, is a major undertaking in which the Pentagon is investing a lot of resources. But "there's no recognition of that" in FISMA, Lentz said.Implementing standardized configurations for computers of all types, including desktop, notebook and handheld, is another move that significantly improves security by enhancing configuration management and streamlining patch management. But the law doesn't include a grade for that, he said."We clearly have to do much better in creating metrics" for FISMA, Lentz said. "All the things we're talking about now are output measures, not outcome measures.""I think the agencies should have brought up" how to credit departmentwide improvements as an issue at the hearing, said a Government Reform Committee staff member. "Agencies might make a huge push in one year, focusing on one or two areas, [but] sometimes it requires so much effort, it's hard to sustain it."Similarly, the committee began to explore why such a dichotomy has emerged in the FISMA scores, with the largest departments getting the worst grades, while smaller agencies either have the best grades or show greater progress from previous years' results.Particularly alarming were the scores of the departments of Defense and Homeland Security, which both got an F.At the hearing, Rep. Diane Watson (D-Calif.) questioned whether the two agencies most responsible for protecting the country are up to the task if they can't even protect their own computer systems.Davis avoided the partisan tone, but wondered aloud if there is such a difference between large agencies and small ones that FISMA is difficult to apply evenhandedly.Karen Evans, OMB administrator for e-government and IT, said it is not surprising there is a difference between the agencies."The overall size, geographic distribution of offices and systems, as well as legacy systems of differing versions [hardware and software] introduce much complexity," Evans said.But as agencies continue to work at FISMA compliance, she said, security will be integrated throughout the lifecycle of systems, and the adoption and implementation of enterprise architectures will further reduce complexity.At the Pentagon, however, that kind of complexity sometimes is unavoidable. The evolution of network-centric warfare requires that systems and networks be configured on the fly, and reconfigured at a moment's notice as a tactical situation changes."When you're in a very dynamic environment, you can have a system today that is certified. Then its three-year certificate expires, [and] it goes from green Nov. 30 to red Dec. 1," Lentz said.At Homeland Security, the challenge of raising FISMA scores is just one obstacle to integrating all the disparate parts into the three-year-old agency, CIO Scott Charbo said at the hearing.In October, only 26 percent of the department's approximately 700 systems had been accredited; by the end of February, more than 60 percent of the systems had been accredited, he said, adding that reaching 100 percent by the end of the fiscal year is "on track."Patience Wait is a staff writher with Government Computer News. She can be reached at pwait@postnewsweektech.com.

Not the whole story
Bridging the gap

Source: Government Reform Committee
Not the whole story
Bridging the gap
NEXT STORY: Buy Lines: 'Big A' acquisition is here to stay

